IT Security for SME’s
The cybersecurity threat landscape is constantly changing. Cybercriminals are always looking for new ways to compromise your organisation’s network and data. According to a study by Trend Micro, approximately 3.5 cyber attacks occur every second. These attacks are not limited to larger organisations. Cybercriminals are not picky about their victims, and all too often it is the small and medium-sized businesses that fall victim, primarily due to the perceived cost of implementing a robust cybersecurity defence.
At Intuity Technologies, we have invested a great deal of time in investigating cyber defence technologies and techniques. We have created a cybersecurity defence service that will provide end to end protection from internal, external and emerging cyber threats using the best in class security monitoring, alerting and remediation tools that are cost-efficient and affordable for SME organisations.
This is the first in a series of blogs that will inform SME organisations about current and emerging threats that traditional security tools find difficult to defend against. In this first instalment, I will examine why it is important for SME organisations to do more than say they take IT security seriously.
Why cybersecurity is more important than ever?
It can be simplified to five points as described on consultancy.uk (Button, 2019).
- The rising cost of breaches, recent statistics suggest that the financial cost of data breaches for organisations is £20,000 to remediate, however, this does not include the cost of lost future business caused by the reputational damage.
- Increasingly sophisticated hackers, the days of a lone person sitting in a basement trying to break into company networks are long over. Today’s hackers are organised and very well-funded. They trade in data and are willing to invest large amounts of time and money in stealing your information in order to fund their criminal organisations.
- Widely available hacking tools – There is no longer a need for criminals to employ highly skilled computer scientists to develop hacking tools. These tools are available to freely download from the internet and there is no shortage of tutorials online to instruct criminals on how to use the tools to their maximum effect.
- A proliferation of IoT (Internet of Things) devices – Put simply, your IT infrastructure is not restricted to servers and PCs in the office anymore. In today’s online connected world, any device that connects to the internet is a possible source of a data breach. CCTV systems, company mobile phones, printers, scanners etc. can all provide a source for a potential breach.
- Tighter Regulations – We are now over a year since the introduction of GDPR, which means that organisations are required to take better care of the personal data that they hold. If an organisation does not take the appropriate technical and organisational measures to protect personal data, regularly review controls, plus detect, investigate and report breaches then they will face heavy fines. British airways record-breaking £183 million fine for having poor security arrangements to protect customers credit card data is a prime example (Porter, 2019)
Why would my organisation be targeted?
If you have an online presence, i.e. a connection to the internet, then you are susceptible to be a victim of data breaches. Your organisation will not need to be specifically targeted, criminals rely on bots to constantly scan the internet looking for weaknesses in your organisation to infect your systems with malware. The size of your organisation is irrelevant to criminals who are simply looking for a pay-out, and by using automated hacking tools, they scan the internet 24x7x365 looking for their next victim.
It does not matter to hackers if your organisation has five or five hundred employees. In most cases, they use a wide variety of perimeter attack and user phishing tools to target IP address and users email addresses. The Verizon breach report 2019 (Verizon Enterprise, 2019) is a detailed cross-sector security breach report that details attack vectors used and industry responses to cyber-attacks. There are a couple of findings that are of interest to SME organisations.
Firstly, we see that 43% of breaches reported involved small businesses. The primary reason for such a high percentage of attacks on small business is due to the lack of investment in security attack defence.
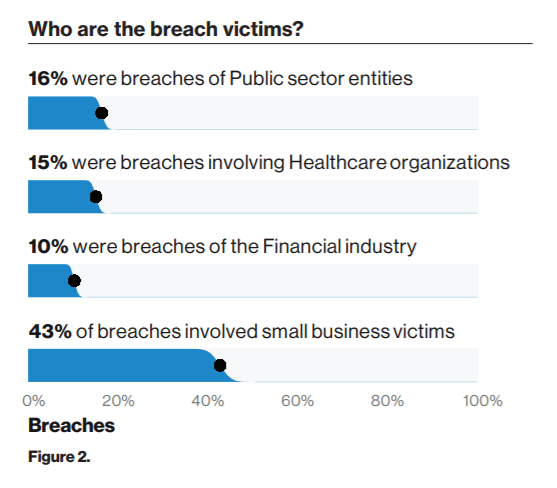
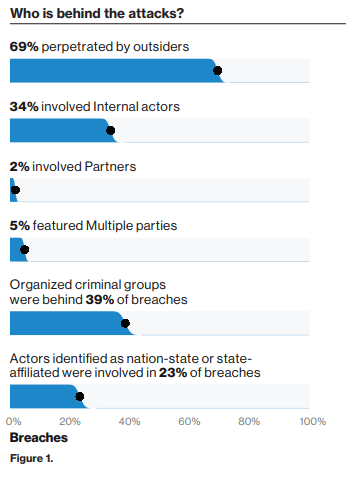
Secondly, it is important to note that security breaches can be instigated from internal sources, disgruntled or compromised employees account for over one-third of data breaches.
Preventing a breach
There is no silver bullet that will guarantee that your organisation will not get breached, the best option is to employ a defence in-depth approach. This type of approach uses layers of defence, that when correctly managed, makes the lives of the cybercriminal more difficult and ensures that the risk of a security breach is greatly reduced.
- It is critically important to have an accurate asset list of your organisation’s IT infrastructure, it is impossible to maintain a secure environment if you do not know what devices need to be protected.
- Your perimeter needs to be secure. Although today’s IT perimeter can be diversified between physical infrastructure located in your organisation’s office, cloud infrastructure and mobile devices, a security-focused network design will ensure that users will have access to the applications and data they require while maintaining a secure perimeter against hackers.
Ensure that all operating systems and third-party applications are updated regularly. Applying patches fix vulnerabilities that have been identified in operating systems and third-party applications. - Review access to your organisation’s data, remember 39% of data breaches come from internal sources. Users who do not need to access specific datasets, should not have access to that data set.
- Audit your infrastructure and data access regularly. Ideally, a change management process should be implemented and maintained.
- Deploy a spam filter to weed out malicious emails.
- Deploy a web filter to prevent users from accessing websites that may contain malicious code.
- Regular user training is important to keep users aware that the threat of phishing attacks are a constant risk and users should not be allowed to become complacent. The training effectiveness should be audited by implementing attack simulations.
Over the coming series, we will highlight some of the emerging threats that will, unfortunately, become more common in the coming months. Intuity Technologies have implemented defences against these threats in several organisations and are continuously monitoring these customer networks to make sure they do not become a statistic.
If you need help managing your IT Security, please contact us at sales@intuity.ie or call 0818 987 900.
References
Button, A. (2019). Five reasons cybersecurity is more important than ever. [online] Consultancy.uk. Available at: https://www.consultancy.uk/news/18435/five-reasons-cyber-security-is-more-important-than-ever [Accessed 16 Jul. 2019].
Porter, J. (2019). British Airways faces record-breaking GDPR fine after data breach. [online] The Verge. Available at: https://www.theverge.com/2019/7/8/20685830/british-airways-data-breach-fine-information-commissioners-office-gdpr [Accessed 19 Jul. 2019].
Verizon Enterprise. (2019). 2019 Data Breach Investigations Report. [online] Available at: https://enterprise.verizon.com/resources/reports/dbir/ [Accessed 16 Jul. 2019].
Oops! We could not locate your form.
